
LISP is a STOP/DJVU family of ransomware-type infections. This type locks
your private files (videos, images, documentations). Then your files' name
will end by this new extension “.lisp” . So, you can’t obtain access to them
at all.
This ransomware family "STOP / DJVU" has more than 260 extensions.
Lisp was Discovered in 19/11/2020, it can encrypts all popular file
types. Quickly as the file encryption is effectively achieved, so users
can't get access to them. Lisp virus add its own “.Lisp” to all the
encrypted data. For instance, the file “timesheet.xls”, after get crypted
by Lisp, will be titled as “timesheet.xls.lisp”.When the encryption is
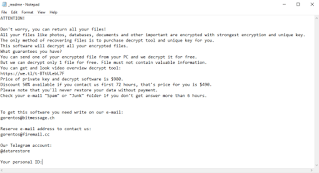
accomplished, lisp will put text document (_readme.txt) into all the
folders that keep the encrypted files.
The used technique for file's encryption by Lisp will released an unique
decryption key, which is definitely unique for each computer system.
The needed key is hosted on a special server under the total control by
the attacker who have actually launched the Lisp infection into the
internet joined by each the victim id, the users are told to contact the
attackers through e-mail or by telegram to pay the ransom in the quantity
of $980 and this quantity will have 50% discount rate, that mean the
ransom amount falls to $490 if the victim pay for them within 72
hours.
We highly recommend that you do not pay the ransom, There is no warranty
that these online cyber criminals will keep their promises, the victims
may lose their money for nothing.
Also, It's not recommended to contact the frauds as they instruct. Do not
send them your money.
Extension ID:
File Extension: lisp
Type: Ransomware
Family: STOP/DJVU
Description: The ransomware locks all the data stored on your system and requires a
ransom to be paid on your part supposedly to recover your important
files.
Encryption: File encryption by the
ransomware is performed by means of the AES-1024 algorithm encryption.
Once the encryption is completed, to adds its special .lisp extension to
all the files modified by it.
Distribution Method: Adware bundles and software cracks
the Web is now loaded with infections comparable to the Lisp virus. It's
recommended for you to frequently make backups of all your essential
documents to an external storage. like, the USB Flash Drive, external hard
disk drive, or using the cloud data storage services. Keeping the backups
on your system drive is very risky, since the backup may also be encrypted
by the Lisp ransomware.
How can the Lisp ransomware attack your computer system?
This type can hide by using one method from these:
1-
freeware third-party programs.
2- spam e-mails ;
3-
free hosting websites;
4- torrent software.
Opening
these types or clicking on the harmful links might harm the
system.
How to Protect your computer system from the Lisp ransomware
attack?
1. Do not open any suspicious e-mail attachments, specifically if the
sender is unknown for you .
2. Do not install unsecured
freeware.
3. install an anti malware or an anti virus with
last update even if free, to check every file you downloaded it from the
web before opening it.
After you successfully
remove lisp ransomware
like emsisoft then install malware protection or antivirus to protect your
files.





